在Red Hat Enterprise Linux Server Releae 5.5 成功安装ORACLE 10g 后,在客户端配置TNS后,测试是否可以连接到数据块服务器,结果报错: ORA-12170:TNS:连接超时
1:首先检查网络是否能ping通,如下所示,网络是畅通的
2:检查TNS配置(TNS配置也没有问题)
GSP =
(DESCRIPTION =
(ADDRESS =(PROTOCOL = TCP)(HOST = 172.20.36.79)(PORT = 1521))
(CONNECT_DATA=
(SERVER = DEDICATED)
(SERVICE_NAME = gsp)
)
)
3:查看服务器监听服务是否启动
[oracle@wgods ~]$ lsnrctl status
LSNRCTL for Linux: Version 10.2.0.1.0 - Production on 14-DEC-2012 15:51:13
Copyright (c) 1991, 2005, Oracle. All rights reserved.
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=IPC)(KEY=EXTPROC1)))
STATUS of the LISTENER
------------------------
Alias LISTENER
Version TNSLSNR for Linux: Version 10.2.0.1.0 - Production
Start Date 14-DEC-2012 13:15:28
Uptime 0 days 2 hr. 35 min. 45 sec
Trace Level off
Security ON: Local OS Authentication
SNMP OFF
Listener Parameter File /database/oracle/product/dbhome/network/admin/listener.ora
Listener Log File /database/oracle/product/dbhome/network/log/listener.log
Listening Endpoints Summary...
(DESCRIPTION=(ADDRESS=(PROTOCOL=ipc)(KEY=EXTPROC1)))
(DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=wgods)(PORT=1521)))
Services Summary...
Service "PLSExtProc" has 1 instance(s).
Instance "PLSExtProc", status UNKNOWN, has 1 handler(s) for this service...
Service "gsp" has 2 instance(s).
Instance "gsp", status UNKNOWN, has 1 handler(s) for this service...
Instance "gsp", status READY, has 1 handler(s) for this service...
Service "gspXDB" has 1 instance(s).
Instance "gsp", status READY, has 1 handler(s) for this service...
Service "gsp_XPT" has 1 instance(s).
Instance "gsp", status READY, has 1 handler(s) for this service...
The command completed successfully
4:使用tnsping命令检查,报TNS-12535: TNS: 操作超时,这时我们可以肯定是防火墙的问题了
C:\Users\kerry>tnsping 172.20.32.79
TNS Ping Utility for 32-bit Windows: Version 11.2.0.1.0 - Production on 14-12月-2012 15:47:15
Copyright (c) 1997, 2010, Oracle. All rights reserved.
已使用的参数文件:
E:\app\kerry\product\11.2.0\dbhome_1\network\admin\sqlnet.ora
已使用 EZCONNECT 适配器来解析别名
尝试连接 (DESCRIPTION=(CONNECT_DATA=(SERVICE_NAME=))(ADDRESS=(PROTOCOL=TCP)(HOST=172.20.32.79)(PORT=1521)))
TNS-12535: TNS: 操作超时
对于防火墙问题,我们可以有两种解决方案:
1:关闭防火墙(这种方案不怎么好,关闭防火墙,会带来许多安全隐患)
[root@wgods ~]# service iptables stop
Flushing firewall rules: [ OK ]
Setting chains to policy ACCEPT: filter [ OK ]
Unloading iptables modules: [ OK ]
2:修改iptables,开放1521端口,允许1521端口被连接
2.1 编辑iptables文件,添加-A RH-Firewall-1-INPUT -p tcp -m state --state NEW -m tcp --dport 1521 -j ACCEPT记录。
[root@wgods sysconfig]# vi iptables
# Generated by iptables-save v1.3.5 on Fri Dec 14 17:03:58 2012
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [1749:243629]
:RH-Firewall-1-INPUT - [0:0]
-A INPUT -j RH-Firewall-1-INPUT
-A FORWARD -j RH-Firewall-1-INPUT
-A RH-Firewall-1-INPUT -i lo -j ACCEPT
-A RH-Firewall-1-INPUT -p icmp -m icmp --icmp-type any -j ACCEPT
-A RH-Firewall-1-INPUT -p esp -j ACCEPT
-A RH-Firewall-1-INPUT -p ah -j ACCEPT
-A RH-Firewall-1-INPUT -d 224.0.0.251 -p udp -m udp --dport 5353 -j ACCEPT
-A RH-Firewall-1-INPUT -p udp -m udp --dport 631 -j ACCEPT
-A RH-Firewall-1-INPUT -p tcp -m tcp --dport 631 -j ACCEPT
-A RH-Firewall-1-INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A RH-Firewall-1-INPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT
-A RH-Firewall-1-INPUT -p tcp -m state --state NEW -m tcp --dport 25 -j ACCEPT
-A RH-Firewall-1-INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A RH-Firewall-1-INPUT -p tcp -m state --state NEW -m tcp --dport 23 -j ACCEPT
-A RH-Firewall-1-INPUT -p tcp -m state --state NEW -m tcp --dport 1521 -j ACCEPT
-A RH-Firewall-1-INPUT -j REJECT --reject-with icmp-host-prohibited
COMMIT
# Completed on Fri Dec 14 17:03:58 2012
~
~
~
~
~
"iptables" 24L, 1212C written
2.2 重启iptables服务
[root@wgods sysconfig]# service iptables restart
Flushing firewall rules: [ OK ]
Setting chains to policy ACCEPT: filter [ OK ]
Unloading iptables modules: [ OK ]
Applying iptables firewall rules: [ OK ]
Loading additional iptables modules: ip_conntrack_netbios_ns ip_conntrack_ftp [ OK ]
2.3 保存新增的规则,以免下次重启机器后,配置规则失效
[root@wgods sysconfig]# service iptables save
Saving firewall rules to /etc/sysconfig/iptables: [ OK ]
2.4 查看1521端口是否开放,允许连接(见红色部分)
[root@wgods sysconfig]# iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain RH-Firewall-1-INPUT (2 references)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 255
ACCEPT esp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT ah -- 0.0.0.0/0 0.0.0.0/0
ACCEPT udp -- 0.0.0.0/0 224.0.0.251 udp dpt:5353
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:631
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:631
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:21
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:25
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:23
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1521
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
[root@wgods sysconfig]#
从客户端用PL/SQL Developer连接数据库,问题解决。
在客户端配置TNS测试报错ORA-12170:TNS:连接超时
2019-11-18 15:42ORACLE教程网 Oracle
在Red Hat Enterprise Linux Server Releae 5.5 成功安装ORACLE 10g 后,在客户端配置TNS后,测试是否可以连接到数据块服务器,结果报错:ORA-12170:TNS:连接超时
延伸 · 阅读
- 2022-03-09关于UDP服务器客户端编程流程介绍
- 2022-03-03java WebSocket客户端断线重连的实现方法
- 2022-02-22C++实现一个简单的SOAP客户端
- 2022-02-22C#客户端程序调用外部程序的3种实现方法
- 2022-02-16C++编写的WebSocket服务端客户端实现示例代码
- 2022-01-20使用Go实现TLS服务器和客户端的示例
- Oracle

Linux中Oracle数据库备份
在Linux中Oracle数据库备份的方法有很多,就像mysql一样可以使用不同方法进行备份oracle数据库 ...
- Oracle

Oracle查看表结构命令详解
这篇文章主要介绍了Oracle查看表结构命令详解的相关资料,需要的朋友可以参考下 ...
- Oracle

oracle 优化的一点体会
oracle 优化的一点体会大家可以参考下,提升运行效率。 ...
- Oracle
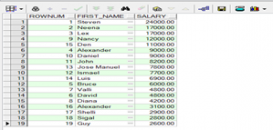
oracle中利用关键字rownum查询前20名员工信息及rownum用法
这篇文章主要介绍了oracle中利用关键字rownum查询前20名员工信息,本文通过代码给大家简单介绍了ORACLE 中ROWNUM用法,非常不错,具有一定的参考借鉴价值,需...
- Oracle

oracle使用instr或like方法判断是否包含字符串
使用contains谓词有个条件,那就是列要建立索引,本节主要介绍了oracle使用instr或like方法判断是否包含字符串,需要的朋友可以参考下 ...
- Oracle
![[Oracle] dbms_metadata.get_ddl 的使用方法总结 [Oracle] dbms_metadata.get_ddl 的使用方法总结](/images/defaultpic.gif)
[Oracle] dbms_metadata.get_ddl 的使用方法总结
以下是对Oracle中dbms_metadata.get_ddl的用法进行了详细的分析介绍,需要的朋友参考下 ...
- Oracle
Oracle数据库由dataguard备库引起的log file sync等待问题
这篇文章主要介绍了Oracle数据库由dataguard备库引起的log file sync等待,本文给大家介绍的非常详细,对大家的学习或工作具有一定的参考借鉴价值,需要的朋...
- Oracle

oracle 动态AdvStringGrid完美示例 (AdvStringGrid使用技巧/Cells)
本方法实现用常量和常量数组完美创建和控制动态TAdvStringGrid。 ...